
[ad_1]
The Microsoft 365 business assist workforce resolves buyer assist instances and gives assist that will help you achieve success and understand the total potential and worth of your buy. Our assist companies lengthen throughout all the lifecycle and embody pre-sales, onboarding and deployment, utilization and administration, accounts and billing, and break-fix assist. We additionally spend a substantial period of time working to enhance the supportability of Microsoft 365 companies to scale back the variety of points you expertise in addition to reduce the time and effort it takes to resolve your points in the event that they do happen.
We’re excited to welcome one in every of our Microsoft 365 Supportability workforce members to speak extra about easy methods to handle safety settings for customers.
Brian: Welcome John! Let’s begin with somewhat about your function within the CSS Trendy Work Supportability workforce and what you’re targeted on nowadays.
John: Certain. My title is John Inman and I’m a Senior Supportability Program Supervisor protecting Id and Azure Lively Listing (Azure AD) with Microsoft 365. This consists of situations with safety, multi-factor authentication (MFA), single sign-on, and synchronization with Azure AD Join. I spend most of my time engaged on function and repair enhancements, self-help and diagnostics, and troubleshooting property for our assist engineers. I additionally look ahead to rising points our prospects are reporting and work with the workforce to get forward of these with options.
Brian: Safety is unquestionably high of thoughts for lots of our prospects. What are you engaged on within the safety space with Azure AD engineering for Microsoft 365?
John: I’d wish to share somewhat background first… as a part of an ongoing effort to scale back compromised accounts, Microsoft has applied safety insurance policies that guarantee our prospects are safe by default.
For instance, the rollout of the Safety Defaults coverage for newly created Microsoft 365 tenants on all license ranges started in 2019 and completed in 2020. That meant that each one tenants created after October 22, 2019, had the Safety Defaults coverage utilized by default-unless the tenant admin disabled it after tenant creation. Safety defaults requires two-factor authentication for all customers and requires a consumer to register for MFA inside 14 days.
For some admins, this didn’t work for varied causes. Often, it’s as a result of some customers had been nonetheless utilizing Fundamental authentication indirectly or had service accounts that may’t use two-factor authentication. For these tenants, we proceed to suggest Conditional Entry insurance policies or per-user MFA settings.
The most recent information is that safety defaults is now rolling out in 2022 for current Microsoft 365 tenants who haven’t already utilized MFA and have but to allow safety defaults, Conditional Entry insurance policies, or per-user MFA settings.
So, with all this in thoughts, making it as simple as doable for admins to safe their tenant and handle MFA are the explanations behind the creation of the brand new Configure Multi-Issue Authentication function within the Microsoft 365 admin middle. Previous to this, and with the rollout of Safety Defaults in 2019–2020, our admins needed to go to the Azure Portal to handle Safety Defaults, some didn’t know the place to search out it initially or weren’t anticipating MFA–it led to a number of assist calls.
Brian: Wow, so the brand new Configure Multi-Issue Authentication function will make it simpler for Microsoft 365 admins to safe their customers. So how do admins use this to handle MFA, Safety Defaults or Conditional Entry insurance policies, and the way is that altering precisely?
John: Managing MFA, safety defaults and Conditional Entry insurance policies has historically been carried out by way of the Azure Portal. Whereas this technique to handle safety is efficient and is completely nonetheless a very good possibility, we acknowledged that many admins don’t frequently use the Azure Portal–some by no means do. So, now we’ve the potential within the Microsoft 365 admin middle too!
With this, admins can handle MFA, Conditional Entry insurance policies and safety defaults from inside Microsoft 365. That is accessible to any World admin, has context-sensitive assist, and solely exhibits the choices which are accessible for that license. There are hyperlinks or hover-over assist for added explanations at every step together with suggestions hyperlinks. Oh, and that suggestions is reviewed frequently too; it doesn’t simply disappear into the ether.
Managing MFA, Conditional Entry and safety defaults can nonetheless be achieved within the Azure Portal, for admins preferring to handle it there. Nothing is being eliminated there-we simply need our prospects safe!
Listed below are just a few snapshots of the configuration beginning with the preliminary splash display that features an outline and stats for the variety of admins protected by MFA inside the final month.
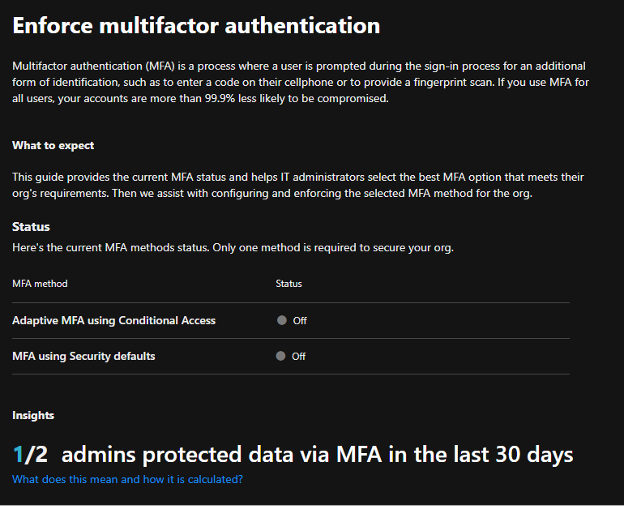
On the subsequent display, you select whether or not to make use of Conditional Entry insurance policies or safety defaults. These choices are tailor-made to the license stage of the tenant. If the tenant license helps Conditional Entry, context-sensitive assist will likely be displayed for that. We additionally suggest Conditional Entry if doable because it gives essentially the most flexibility and safe choices in your surroundings.
The Safety Default coverage applies an MFA requirement throughout all the tenant and blocks legacy authentication. With safety defaults, there are not any provisions for excluding particular consumer accounts from the coverage requirement. Per-user or Conditional Entry insurance policies for MFA must be applied if the tenant has necessities for primary/legacy authentication.
With Conditional Entry insurance policies, you may exclude sure accounts, akin to an older e-mail shopper, printer account or different software that will proceed to require primary/legacy authentication strategies, or customers that won’t have entry to a cellphone for two-factor authentication.

There are some primary templates that permit an admin to shortly deploy MFA utilizing pre-defined Conditional Entry coverage choices. Extra data is accessible below the “Be taught extra” part.

On this subsequent display for Conditional Entry, you may present a number of customers or teams to exclude from the coverage. This may be particularly helpful to nonetheless apply safety throughout your tenant whereas excluding a number of particular accounts utilizing legacy software, akin to an account used for SMTP, printing, backup, or a service account.
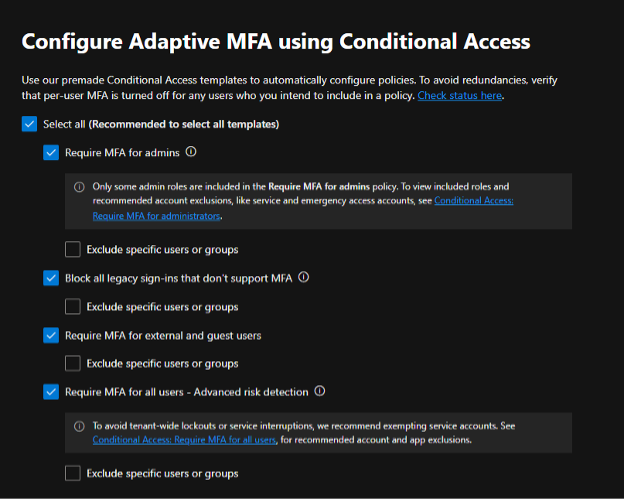
In case your license doesn’t assist Conditional Entry insurance policies, you may shortly activate/off safety defaults in your tenant. This setting will apply the Safety Defaults coverage to your tenant for all customers. The setting can merely be toggled on or off as proven on the backside of this display. If you should configure per-user MFA settings that may nonetheless be achieved within the Azure Portal, too.
Vital: Admins ought to full the registration for MFA inside the 14-day interval after enabling safety defaults.
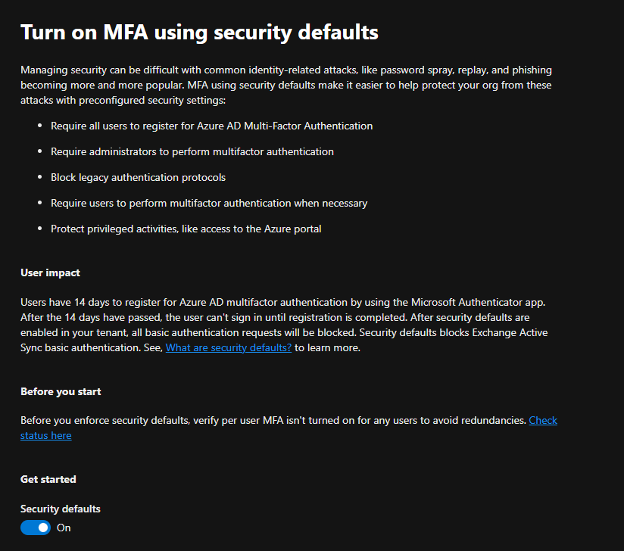
Lastly, the abstract display will present which coverage you’ve utilized earlier than exiting. Within the instance beneath, safety defaults was utilized, and a hyperlink is offered to handle it once more in case you change your thoughts.

Brian: Thanks John, for the detailed clarification and step-by-step! Any ultimate phrases earlier than we go?
John: We hope directors discover the choice to configure MFA by way of the Microsoft 365 admin middle useful in deploying and managing MFA settings. We consider it’s a fast and straightforward strategy to safe your tenant utilizing ready-to-apply safety settings, such because the Safety Defaults or Conditional Entry insurance policies relying in your license.
Take a look at these useful sources for extra data:
To configure MFA by way of the Microsoft 365 admin middle:
Safety Defaults:
For a comparability of MFA capabilities by license:
John Inman is a Senior Supportability Program Supervisor within the CSS Trendy Work Supportability workforce targeted on Id and Azure AD with Microsoft 365.
Brian Stoner is a Director within the CSS Trendy Work Supportability workforce the place he leads a workforce of technical and enterprise program managers.
The CSS Trendy Work Supportability workforce delivers modern self-help options and diagnostics, in-service enhancements, and assist packages to assist prospects get most worth from their Microsoft 365 business subscriptions and create an easy-to-use, related assist expertise.
Proceed the dialog by becoming a member of us within the Microsoft 365 neighborhood! Need to share finest practices or be part of neighborhood occasions? Change into a member by “Becoming a member of” the Microsoft 365 neighborhood. For ideas & methods or to remain updated on the newest information and bulletins immediately from the product groups, be certain to Observe or Subscribe to the Microsoft 365 Weblog area!
[ad_2]

